-
Posts
41 -
Joined
-
Last visited
Content Type
Profiles
Pokédex
Portal
Technical Documentation
Pages
Tutorials
Forums
Events
Downloads
Gallery
Blogs
Posts posted by Albert930208
-
-
For example. A Magnemite from Lono 0081 - Magnemite - FA196977ABE9.pk9must be Shiny Locked.
but... what if I make it to shiny. PkHex still says it's Legal.
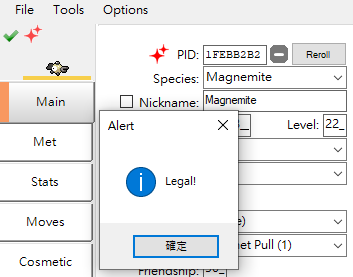 0081 ★ - Magnemite - CE0F6977ABE9.pk9
0081 ★ - Magnemite - CE0F6977ABE9.pk9
-
I also have the same question, I'm curious too.
-
I have investigated all the methods for obtaining Manaphy and Phione. The only way to obtain them, and therefore inherit their ball type, is through encounters in Legend Arceus. However, the balls used in ancient times will be transformed into 'Strange Balls.'
And all of the encounters ways for them, are only be in Poké Ball or Cherish Ball.So, based on this, I assumed that all Phiones obtained from eggs would be in Poké Balls. However, PKHeX indicates that there are various other selectable balls that are considered legal. Have I overlooked something?"
-
11 minutes ago, Nuren said:
And this is how you do it:
I am repeating myself at this point. I will not provide all the information you want, or any simple yes/no answers, because:
- There is too much information even if I wanted to provide all of it. I could write a textbook. There is no easy 15-minute tutorial to become an expert in Pokémon legality.
- Context for the Pokémon matters, and the answer will change for every case.
- You are asking for highly technical information beyond PKHeX legality checks, in a manner that can easily be used to help people lie to others. I am not interested in breaking the rules of the site, or providing public information that will be used for harm over good.
- Your question does not align with the topic of this thread. If you only wanted to help regular players who can access a PKM file hack check, we have provided the answer multiple times in this thread. (Look for strictly illegal traits, using PKHeX if you want. Then look for improbable traits. Assess the situation. Make your own decision.)What I know, I have learned from years of playing the games, experimenting, and observing. You can do the same thing by viewing the data of legitimate Pokémon in PKHeX. Many older mechanics are documented on the internet. This is what we are encouraging you to do when we say that you must research what you want to know.
Thank you for your response and the advice you've provided. The suggestion you mentioned, which involves viewing the data of legitimate Pokémon in PKHeX, is something I've been doing and is already familiar to me. Even if I have new questions or need to compare data, I can rely on examining PKHeX's database or using search engines to find answers.
I completely understand your reluctance to inadvertently assist malicious hackers who disrupt the game, as this is a concern I've also considered. It's an assumption that even basic PKHeX users might contemplate. I have a request: aside from the straightforward data comparison for verifying legitimacy, how can I further learn about highly technical information beyond PKHeX legality checks? You don't need to reveal violations or your concerns. Even providing a general direction would be a significant help, allowing me to pursue learning and data collection. Thank you.
-
It seems we're going around in circles with the same question. I'm not incapable of comprehending all the content, although there might be a slight margin of error due to translation, the general understanding is pretty much the same.
The reason I have more questions is because you mentioned :
48 minutes ago, Nuren said:You are asking me to tell you whether a hack is good enough or not that a human cannot distinguish. These details will never affect anyone playing the story with hacked/legal Pokémon, but will be used to lie to and trick others into thinking their Pokémon are legitimate. You are asking me to write an absolute massive amount of information that is only going to help people cheat.
My understanding of this statement would be that there indeed are deeper techniques in modifying Pokémon, and it aligns with my conjecture. Since you have concerns, I'm not seeking to know the specifics; I just want to confirm whether my assumption that there are indeed more sophisticated techniques in Pokémon modification is correct. And when you mentioned:
48 minutes ago, Nuren said:The "non technical" player needs to become a "technical" player at this level.
it's exactly what I'm attempting to do.
-
9 minutes ago, Nuren said:
I feel like you are still trying to get an answer to a question that I said is too complex to answer. I am not going to provide an answer for every scenario you can think of. It is up to you to do the research yourself, like all of us in this thread have told you already. Pick the game, pick the encounter, research it thoroughly. Research how a Pokémon can be changed in game, and how you can move them around. Then answer it yourself.
I think that you are conflating the different levels and abilities for people to hack check. Your question for this thread is for non technical users to hack check, which to me implies casual players who do not have CFW. This has been answered already (look for impossible values, then look for improbable traits).
I apologize for any confusion caused, as I am not a professional hacker, I am not able to clearly distinguish the "different levels and abilities of hackers" you mentioned. I also deeply apologize for any misdirection caused by the title; I mistakenly assumed that all users on this forum are familiar with pkhex. Therefore, I defined "non technical users" as those without programming backgrounds, rather than strictly users who have no exposure to CFW (custom firmware).
I am not completely avoiding CFW now, which is why I'm seeking to learn more details.
-
23 minutes ago, Nuren said:
I cannot provide a better answer than what I have already provided. The answer is "It depends."
You must research the specific encounter, the specific details that are different from a legitimate Pokémon, and make the decision yourself. Both "yes" and "no" are wrong answers depending on the case.
I can try to compose Pokémon data for you to inspect its legality, but I am not a professional hacker. Even expert hackers can make mistakes at times, so obviously non-compliant Pokémon data (e.g., a Pokémon knowing Thunder but not having the TM Mark selected) can be distinguished. 0362 ★ - Glalie - 67F4D90E4436.pk90462 - ジバコイル - D00D33DCCEA0.pk90890 ★ - 無極汰那 - 1A77BB352663.pk9
I must reiterate my question to ensure there is no misunderstanding leading to a meaningless communication loop. A Pokémon from a Tera Raid Battle can have its data matched through RNG calculations. Is there a similar way for a wild Pokémon, allowing us to trace if its data could naturally occur in the game through encounters?
-
7 minutes ago, Nuren said:
> can I create a Pokémon that is both legitimate and reasonable?
Created Pokémon are never legitimate. They can be legal and reasonable.That's exactly what I meant. A Pokémon that might comply with the game's rules but wasn't naturally obtained – can I distinguish it by any way? I simply need a yes or no.
-
24 minutes ago, Nuren said:
If a user perfectly recreates a legitimate Pokémon, then there is no way you can tell. Most people who gen Pokémon do not perfectly recreate legitimate Pokémon. I am not going to go into this in more detail because that would be straight up telling people how to create better hacks in order to fool other people.
If you are asking about clones, the only way to verify a clone is to see another copy of it, assuming the Pokémon is not a natural clone.
This is like asking "Is it possible to commit a perfect crime and never be caught?" It may be easier to think of hack checking like a court case. You must look at the suspect, the circumstances of the crime, any evidence that is available, and what any witnesses can tell you.
The only ways to know if a Pokémon is legitimate is for you to either catch it yourself (and know all the circumstances of capture), or observe someone else do it and then check their console/setup to ensure no cheats are active. That means for most cases of Pokémon you receive from others, you cannot be 100% sure that it is legitimate. In the same way, the suspect knows 100% whether they committed the crime or not, but the jury may not know. Everything else is going to be a level of suspicion depending on the user and the mon. Here are some examples to think about:
If your best friend says "I caught a shiny Pikachu legitimately with no cheats/hacks" do you believe them?
What if your best friend's Pikachu was Timid 31/0/31/31/31/31 on top of being shiny, do you still believe them?What if a random stranger on the internet told you the two above, do you believe them?
What if a user with a known hacker OT/TID on the internet told you the two things above, do you still believe them?I completely understand your example regarding the 6IV shiny Pikachu. This is how most players nowadays judge whether a Pokémon is hacked based on common sense, but these judgments are made on the "legitimacy" level.
I sought information about Pkhex to gain a deeper understanding on the "legality" aspect. I've learned the basic functionalities of Pkhex. Now, I'm working on understanding more and planning to convey the information I've gathered in a simpler and more understandable way to players who don't use any third-party hacking software. My goal is to engage the audience and improve the gaming environment, even if the impact is minimal – every bit of change matters.
I understand if you're hesitant to provide detailed instructions on distinguishing hacks, as I've also considered the risks associated with that.
I just want a straightforward answer to a question. I believe the answer to this question won't lead to the concerns you mentioned earlier. My question is, if I only use the default six categories in Pkhex (Main, Met, Stats, Moves, Cosmetic, OT/Misc) for editing, along with the information from the Mystery Gift/Encounter Database, without altering any other settings or using any third-party tools beyond Pkhex (such as RNG calculators), can I create a Pokémon that is both legitimate and reasonable?
If this is possible, it would indicate that there might not be a simple method to discern more sophisticated fabricated Pokémon. If it's not possible, then it suggests that there are hidden data that can be manipulated and more advanced ways to expose them. I'm hoping to get an answer to this question.
-
54 minutes ago, Nuren said:
No, this is not fully accurate. I think you are confusing legality and legitimacy. This is probably a problem with translators giving the same word in other languages, but the two words are used differently when discussing hacked Pokémon.
Again, it will depend on the encounter. Some encounters are more thoroughly checked by PKHeX, others are not. When knowledge is fully known, yes it is possible to fully determine the legality of a wild-caught Pokémon. Legality checks are always improving, so something that is currently not flagged may be flagged in the future. If you rely on a program like PKHeX and want to know how good each check is, that would still require you to do research into the encounter and the program.
Remember that legality is not legitimacy. PKHeX does not do legitimacy checks. It does legality checks. Legality is whether it is possible to obtain a Pokémon that has those details. A legitimate Pokémon was obtained properly through the correct methods in-game. Fully determining legality does not fully determine legitimacy. A hacked Pokémon can be legal, but a hacked Pokémon is by definition not legitimate. The only way to know that something is fully legitimate is to know the exact circumstances used to capture the Pokémon. Otherwise, without knowing how it was obtained, the best you can do is compare to what is known to be possible.
As I said before, it is possible to prove something is 100% hacked if it has 100% impossible features. Otherwise, you should take into account how likely that Pokémon is. It would be wrong to say that a 6 IV wild shiny Pokémon with 1/549755813888 chance is equally likely as a random IV, nonshiny Pokémon with nothing outstanding, simply because there are no strictly illegal features. PKHeX does not rate whether one Pokémon is more likely than another; that is for the user to research and understand.
Yes, it is possible for a hacker to completely copy the details of a legitimate Pokémon. But you are not likely to see people hacking Pokémon that are exactly the same as random wild Pokémon. You have to look at the Pokémon yourself, research to know what is possible to figure out the chance of it occurring, and make the decision based on that knowledge. PKHeX can tell you that the values are possible, but that does not mean a sensible human should believe that odds of 1 in billions is as reasonable as a random Pokémon.
Most trade communities do not expect casual users to have full access to the Pokémon data and research, so that is why they use methods such as listing known hacker OTs and general tells that are more associated with hacked than legitimate Pokémon. For example, Mitsuki.TV is a known streamer who distributes hacks. Yes, it's possible that someone innocent might pick Mitsuki.TV as their name. But do you really think an innocent user picked the same name as a streamer, found a legitimate shiny 6 IV legendary, and then gave it to you for free?
Thank you for your response, and my understanding aligns completely with what you mentioned, including your example of Mitsuki.TV. This current Chat GPT has clearly distinguished between "legality" and "legitimacy" in translation, which makes me more confident in my understanding.
I'm curious about a scenario: If a morally ambiguous player were to have the same reasons as Pokémon World Championship participant Brady Smith, that is, not wanting to spend time on Pokémon breeding and opting for hacked Pokémon, and they modify a Pokémon to be extremely "legitimacy" (for example, non-shiny, low IVs for Hyper Training, not maximum/minimum size, no special marks), would I still have a means to expose them using any third-party tools (such as pkhex)? Do I have a method to identify the source of a Pokémon that possesses both reasonability and legality, and determine whether it's fabricated?
By the way, for an event-gifted Pokémon with all fixed values (such as PID, IVs, Shiny, Height and Weight), is it impossible to distinguish whether it originated from a Mystery Gift, was duplicated, or was fabricated from scratch?
-
1 hour ago, Kaphotics said:
legality, not legitimacy.
I am using ChatGPT to help me translate Chinese into English. I apologize for any inaccuracies in the translation.
1 hour ago, theSLAYER said:Statistics. When you stack multiple improbabilities, the odds in the end is practically impossible. Check out Matt Parker’s breakdown on Dream’s cheated Minecraft run.
There are some cut and dry cases, then there are some that requires nuance and context and tons of research, then there are those are legal and indistinguishable from the real deal but hacked in the hearts of the players.
It’s going to be a lot to unpack and you’re gonna need to read it all up.
Thank you both for your responses. If my understanding is correct...
Currently, there isn't an absolutely accurate method to determine the legality of a wild-caught Pokémon. This means that as long as hackers carefully edit every detail to make the Pokémon appear legitimate, even using software to analyze the Pokémon might not provide certainty about its legitimacy.
It's important not to blindly trust the indications given by PKHeX, as those indications can have a certain level of inaccuracy.
Is the above content accurate?
-
1 hour ago, Nuren said:
The only way to tell that a Pokémon is 100% hacked is to find a trait that is 100% impossible.
If you do not have access to the data and can only view in-game summary screens, that will limit your ability to see impossible traits. Even with access to PKHeX, there are some traits that are highly improbable but still legal.
As others have said before, knowing what is an impossible trait or an improbable trait requires knowledge about the game and encounter. That kind of information could fill textbooks. An impossible trait might be easily visible, such as an impossible Poké Ball or a shiny-locked Pokémon that is shiny. Likewise, an impossible trait may require you to have the data, such as calculating the RNG correlation for SWSH Pokemon which requires hidden values such as PID and EC. Many users use common streamer OTs as a sign that a Pokémon is very likely to be hacked, even if the Pokémon is fully legal. The chance of a random wild Pokémon in SV with no fixed IVs to be shiny and 6 IV is at best 1 in (512 x 32^6) and it's very common for people to use these kind of odds as reason to find a mon suspicious.
You're looking for something like this page, but there isn't a resource with every tell possible for every game. That requires the user to do the research. I believe that page is also not completely up-to-date, so some of the information on there has since changed due to new mechanics.
Thank you for your information, and I can also understand what you're saying. As long as an event's probability isn't 0%, then it can't be considered impossible, even if some hacked Pokémon seem extremely unlikely (like being 6IV, shiny, and Legendary all at once).
However, when it comes to Pokémon encounter methods, shiny locks, and event distributions, you can use PKHeX or online resources to verify the legitimacy of a Pokémon. This is also the most common way of determining legitimacy.
If we judge the rationality of a Pokémon's legitimacy based on "logic," we encounter a challenge: hacked Pokémon are not like counterfeit money where any detail can reveal its authenticity. Hacked Pokémon are more like items produced by original printing machines, indistinguishable unless the printer (hacker) makes a mistake.
In PKHeX, setting aside a few vulnerabilities or bugs, does a system prompt that a Pokémon is "legitimate" necessarily mean it's truly legitimate? Is there a possibility that PKHeX could label a Pokémon as legitimate, but it's because of PKHeX and Nintendo's scrutiny might both miss that it's actually illegal?
Assuming a Pokémon is made up from scratch but logically and legitimately, beyond the "speculation and guesswork" you mentioned earlier, is there any way to "accurately" determine whether a hacked wild Pokémon is hacked, and if so, what method would that be?
-
9 hours ago, theSLAYER said:
I’ve been told the Pokémon you’ve uploaded is so illegal in the latest version of PKHeX, give that a check.
Also, go back to what Kaphotics said as a thought experiment regarding the mon’s legality. Most hackers that doesn’t think things get their Pokémon caught on one of the points there. (You can still get caught even if you go through those points, but baby steps).
The conversation above seems to have deviated from the focus due to the discussion about Magnezone, which was a mistake on my part, and I apologize for that.
Returning to the initial and only question I had: Is there any way, apart from speculation and guesswork, to "accurately" determine whether a wild-caught Pokémon is a hacked one, regardless of whether it involves RNG or any other method? If such a method exists, what is it?
-
10 minutes ago, theSLAYER said:
Literally same Kaphotics. Also the amoongus shown is from SWSH, not SV. SWSH overworld mons has Overworld8 RNG correlations.
And they’ve already spelt out their thought experiment relating to analysis.
Your original question started out from a vanilla player POV, but it now seems to be going towards the “hacker trying to create legal competitive mons”. We’re not into validating legal entries for competitive use, so please steer clear from questions that can be misconstrued to have that kind of intent.
I apologize for the misunderstanding I caused. I've been working on preparing a video about "How to more accurately identify hacked Pokémon," aiming to address any unclear or mistaken points from my previous videos. Here are the links to my YouTube videos to show that I'm not attempting to disrupt the fairness of the game, but rather to convey how to differentiate hacked Pokémon.
I genuinely intend to delve into the details of identifying hacked Pokémon as thoroughly as possible and create a video to educate on this matter. While I understand this might inadvertently help hackers refine their techniques, I've stressed multiple times in the video that I do not endorse or promote any hacking methods. I've also taken precautions by masking anything associated with hacking using mosaic overlays.
I'm sincerely sorry for any confusion I caused, and I hope to receive your understanding and clarification.
Video 1: -
11 minutes ago, Kaphotics said:
My message was intended to be a thought exercise for whoever wanted to investigate it.
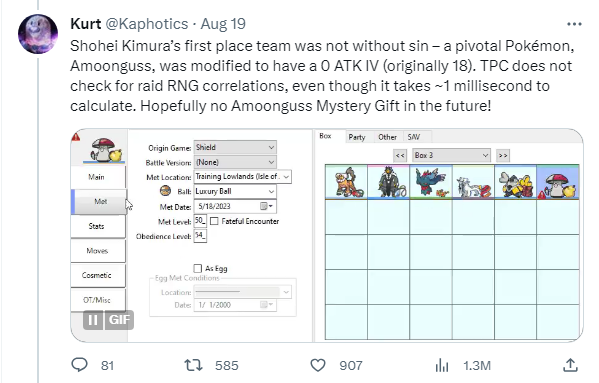
The attachment is illegal, it only learns Thunder via TM yet it doesn't have the TM flag checked.
Regular wild Pokémon in SV do not have any RNG correlation because they use the csprng.
csprng? So does this mean that the attached Pokémon is legitimate and normal except for me forgetting the Thunder move's TM flag? And there's absolutely no way to tell in any manner that this Pokémon is artificially created? This is a screenshot posted by @Kaphotics on Twitter, and I'm curious about how they identify Hacked Pokémon. Also, the source is Training Lowlands (wild Pokémon), and it would be detected that the Atk (IV) was edited?
-
1 hour ago, theSLAYER said:
Read the last point. There’s too much encounter scenarios to reply for every single one of them. You’re gonna need to figure them out for yourselves based on the mons in question (if/when you encounter them)
I apologize for any misunderstanding. It's possible that I haven't fully comprehended your response. It's possible that being a non-native English speaker, I might not fully grasp the intricacies. Let me clarify by providing an example. Is there a way to determine if the attached Pokémon has been fabricated? This is a Pokémon that appears highly plausible, but is entirely fictional in origin.0462 - ジバコイル - 8C3A33DCCEA0.pk9
-
3 hours ago, Kaphotics said:
Break it down into smaller questions.
1. Is the encounter the Pokémon originated from subject to any RNG correlation or pattern?
2. Did the encounter get generated with the correct pattern straight from the database?
3. Is the correlation possible to calculate in near-realtime?
4. Is the correlation calculation implemented in the program?
Good luck answering all for every encounter available in the games.
Thank you for helping me organize these questions. Could anyone please provide the answers to these questions?
-
6 hours ago, theSLAYER said:
If they took the time and effort to hack somewhat competently, no.
And for RNG, you more or less can’t see them without being able to view the data.
Anyhow, even if they didn’t hack competently, well, even so, you won’t really be able to without access to viewing the team’s summary.
if you could view the team’s summary, at least *maybe* a few things will pop out, like multiple a Gen 9 Pokémon being caught on the same date with all perfect IVs (you’ll need the IV judge for that), and maybe a bunch of shinies on the same date even if they aren’t flawless in stats. Maybe they weren’t caught in the correct location.
It’s not gonna be easy for players with access to the data, and even in situations that people has access to the data (like event staff), they may not know what to check.
Anyhow, I believe RNG manipulations isn’t the problem that was highlighted (also I wasn’t answering to that either), but rather it was bad hacks that didn’t take legitimate RNG sequences into account, hence giving a concrete reason to show they were hacked.
The methods of identification you mentioned, such as obtaining multiple perfect Individual Values (IVs) or multiple shinies in a short period, do indeed raise suspicions. However, these indicators can only be used to speculate about the possible illegitimacy of the source and cannot independently infer the legitimacy of the Pokémon.
Regarding the "mismatch between the claimed capture location and the actual capture location," I have a question. If a hacker sets an incorrect encounter location, wouldn't PKHeX not trigger a prompt, indicating that the Pokémon is illegal?
Before addressing that question further, let's assume I'm a savvy hacker. I extract a legitimate wild Pokémon using PKHeX's Encounter Database and carefully attend to details like the date, Poké Ball type, and OT information to maintain realism. Then I edit its IVs (for example, setting Attack to 0) while remaining vigilant about legitimacy. Even though PKHeX indicates that the Pokémon is legitimate, would this approach raise concerns related to RNG?
I've encountered quite a bit of one-sided information, so I'm seeking a more informed explanation. Specifically, I'm interested in the methods of identifying Pokémon through RNG manipulation. It appears to be a potential approach beyond just "legitimacy" and perhaps a more accurate way of making determinations?
-
The recent Pokémon World Championship has sparked significant controversy regarding the fairness of the Random Number Generation (RNG) mechanics in Pokémon. This has also led to increased player attention towards RNG manipulation and the presence of hacked Pokémon. As a player without an engineering background, what approach should I take to ascertain the legitimacy of the RNG associated with Pokémon obtained through various channels, such as Wonder Trade or trading with friends?
Furthermore, if a user adjusts a Pokémon's RNG to make it appear legitimate and conceals the truth of it being a hacked Pokémon, is there no way to verify this deception?
-
On 2/1/2023 at 9:08 PM, SkyLink98 said:
When connecting online, 4 blocks are synced with BCAT: fixed_reward_item_array, lottery_reward_item_array, raid_enemy_array, raid_priority_array. Then, the game generates an uint Identifier block based on those files identifier. The event raids are stored in Flatbuffers structures, as the ROM Raids are.
I want to make a custom 7 star raid. for example, Mewtwo
what files do I needs to edit and what tool do I need for it? -
1 hour ago, theSLAYER said:
Out of curiosity, did you modify the save in any way? Maybe importing raids, editing seeds, that kinda stuff?
Also, the seed of the area is determined and saved. So even if you import the save onto your Switch, the bugged seed is already determined, thus those mons will still show up the same. Or is this save from after you move to a different location, trigger different spawns, then went back to check?
Edit: Also, you probably shouldn't share your save online. These games likely have online save verification similar to PLA, and you wouldn't want to be unable to use your save online.I did import raids. Maybe that's the reason.
By the way. this game save is for testing. it's ok to spread. I only use it on emulator and virtual switch system. -
On 7/16/2023 at 4:51 PM, theSLAYER said:
if the ROM was not edited to begin with, I doubt it. Maybe restart the game, then fly away, then fly back.
Check if your emulator has any mods enabled or something.
Also make sure you're using your own ROM you dumped from your Switch.Bad news. It's not the ROM or Ryujinx's problem.
This bug happened both on emulator and switch.
Here is the game save file. there is a shiny Heracross in the bamboo forest. -
4 hours ago, theSLAYER said:
Also technically happens if you modified the ROM to have many many rerolls. It eventually causes issues and rerolls to similar or same PID with many FF, if I’m not mistaken. Maybe thats going on here?
I did not edit the rom. only the main save file.
Maybe the rom I used was broken from the first time? -
2 hours ago, BlackShark said:
Likely an issue with Ryujinx. Does this happen on your Switch as well?
Maybe? I have never met or heard that



Free Roam Mods for Pokemon SV
in RAM - Switch Cheats
Posted
I found some ways to cut across walls from Pokemon SV with out any hack or save editing.

However, there are still many unreachable areas because of the teleporting
(game will teleport players back to the last safe location if player is too far away the map)
Game Freak places many structures close together.(A fake Mesagoza is being placed above Area Zero and obscured by clouds)
The teleporting restriction prevents me from exploring the void.
I'm looking for a mod. make sure I can fly anywhere without being restricted. Even just changing my camera location helps me tremendously.