Hello, I've been working pretty extensively with editing/exploring Pokemon Rumble (Wii) lately, and I have good reason to believe that there are working passwords that were unreleased to the public (at least in the USA and EU versions of the game). If you look up any page with the list of Rumble passwords, you'll notice that there are many more released Japanese passwords than US/EU passwords. The plan with these passwords was that they were to be released to the public through official means of communication like e-mails or being present on the Pokemon website, but in the West, the game did not garner nearly as much publicity or advertising as it did in Japan, leaving a bunch of these passwords totally unreleased. I want to uncover what these passwords are!
Digging through the game's files, within script.arc.cx ( within the script.arc.cx in the USA folder in the US version of the game), there's a file called CItem_nakama.pkc, and this file contains the data storing passwords and the Pokemon those passwords will yield. Looking at the Pokemon data, I can say with confidence that all of the Pokemon data from these presumably Japan-exclusive passwords are actually present in the US version of the game! Unfortunately, there is a missing piece of the puzzle, which are the values of these passwords themselves. The passwords are not stored in plaintext and instead are stored in what appears to be a 20-byte hashed value. Here is an example of the structure for one Pokemon, in this case the Chimchar in the US version, whose password is 81098384:
I am confident that this hashed value contains the password data because making a slight edit to it invalidates an otherwise valid password, and swapping this data out with another 20 byte value from another password will effectively swap which Pokemon you get from the password. I even successfully transplanted a password from the Japanese version of the game into the US version and got it to work, so the game clearly used the same hashing algorithm across the US/JP/EU releases of the game.
For example, I took the 20 hashed password bytes from Chimchar (US password 81098384) and placed them in front of the data which appeared to be for Shiny Pikachu (US password currently not yet known) , and typing in the password 81098384 gave me this Shiny Pikachu instead of the Chimchar!
I've been aimlessly trying to figure out this hashing algorithm to uncover the rest of these passwords and have had little success, so that's why I'm making this thread to see if anyone might have an idea of how these passwords were hashed. The 20-byte structure of these things SCREAMS SHA1 to me, but I have not yet been able to find something that translates 81098384 into 85a4c68fb2e2e4891f1c458d874159a2
2d0a3cc1.
I noticed that back in 2015, SciresM and SlashMolder managed to figure out the way the passwords were hashed in Pokemon Rumble World (see https://gbatemp.net/threads/request-extract-the-valid-passwords-for-pokemon-rumble-world.386805/#post-5454223), and I've been using SlashMolder's BruteForcer as groundwork for my approach to finding the rest of these passwords and making slight tweaks to the input string to see if I can get the hashed value I'm looking for, but I have not had any success yet. The Rumble games have been using this same 8 digit password structure since 2009, so I can't imagine I'm too far off base here, but my results using 81098384 as an input using the algorithm Rumble World did (via SlashMolder's program) look like this, which look nothing like Rumble Wii's password hash that I'm looking for (85a4c68fb2e2e4891f1c458d874159a22d0a3cc1):
This is my first attempt at anything like this, and I still don't know -too- much about hashing yet, so I could very easily be missing something obvious here, so any suggestions/things to steer me in the right direction towards figuring out how this data was hashed, let me know!
[HELP] Pokemon Rumble (Wii) - Unused Password Hashing question
in ROM - Other Discussion & Help
Posted · Edited by WindyPrairie
Hello, I've been working pretty extensively with editing/exploring Pokemon Rumble (Wii) lately, and I have good reason to believe that there are working passwords that were unreleased to the public (at least in the USA and EU versions of the game). If you look up any page with the list of Rumble passwords, you'll notice that there are many more released Japanese passwords than US/EU passwords. The plan with these passwords was that they were to be released to the public through official means of communication like e-mails or being present on the Pokemon website, but in the West, the game did not garner nearly as much publicity or advertising as it did in Japan, leaving a bunch of these passwords totally unreleased. I want to uncover what these passwords are!
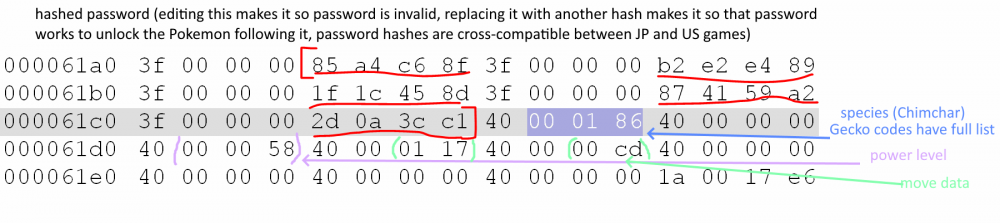
Digging through the game's files, within script.arc.cx ( within the script.arc.cx in the USA folder in the US version of the game), there's a file called CItem_nakama.pkc, and this file contains the data storing passwords and the Pokemon those passwords will yield. Looking at the Pokemon data, I can say with confidence that all of the Pokemon data from these presumably Japan-exclusive passwords are actually present in the US version of the game! Unfortunately, there is a missing piece of the puzzle, which are the values of these passwords themselves. The passwords are not stored in plaintext and instead are stored in what appears to be a 20-byte hashed value. Here is an example of the structure for one Pokemon, in this case the Chimchar in the US version, whose password is 81098384:
I am confident that this hashed value contains the password data because making a slight edit to it invalidates an otherwise valid password, and swapping this data out with another 20 byte value from another password will effectively swap which Pokemon you get from the password. I even successfully transplanted a password from the Japanese version of the game into the US version and got it to work, so the game clearly used the same hashing algorithm across the US/JP/EU releases of the game.
For example, I took the 20 hashed password bytes from Chimchar (US password 81098384) and placed them in front of the data which appeared to be for Shiny Pikachu (US password currently not yet known) , and typing in the password 81098384 gave me this Shiny Pikachu instead of the Chimchar!
I've been aimlessly trying to figure out this hashing algorithm to uncover the rest of these passwords and have had little success, so that's why I'm making this thread to see if anyone might have an idea of how these passwords were hashed. The 20-byte structure of these things SCREAMS SHA1 to me, but I have not yet been able to find something that translates 81098384 into 85a4c68fb2e2e4891f1c458d874159a2
2d0a3cc1.
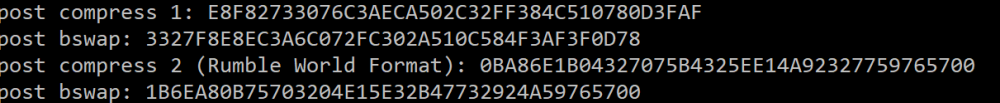
I noticed that back in 2015, SciresM and SlashMolder managed to figure out the way the passwords were hashed in Pokemon Rumble World (see https://gbatemp.net/threads/request-extract-the-valid-passwords-for-pokemon-rumble-world.386805/#post-5454223), and I've been using SlashMolder's BruteForcer as groundwork for my approach to finding the rest of these passwords and making slight tweaks to the input string to see if I can get the hashed value I'm looking for, but I have not had any success yet. The Rumble games have been using this same 8 digit password structure since 2009, so I can't imagine I'm too far off base here, but my results using 81098384 as an input using the algorithm Rumble World did (via SlashMolder's program) look like this, which look nothing like Rumble Wii's password hash that I'm looking for (85a4c68fb2e2e4891f1c458d874159a22d0a3cc1):
This is my first attempt at anything like this, and I still don't know -too- much about hashing yet, so I could very easily be missing something obvious here, so any suggestions/things to steer me in the right direction towards figuring out how this data was hashed, let me know!